It’s a wonderful Friday evening. You’re out enjoying it with some friends, eating dinner at a classy Italian restaurant, telling stories and laughing together as you share a delicious bottle of wine. It’s the perfect end to the week.
As dinner wraps up, you hand the waitress the first card you grab from your wallet, a debit card, and don’t think twice. Moments later, she returns and asks you, quietly, if you have another card they can try. Looking at the debit card in her hand, you put two and two together, and a sinking feeling creeps in.
You pick up your phone and check. Sure enough, your account has a $0 balance. You just deposited your paycheck last week, and have been careful to keep a reasonable balance in there. And it’s gone. All of it.
You can’t begin to understand what happened, as you frantically call the bank, your night utterly ruined. But someone knows. The one who drained your account. The one who entered just the right username and password. The same password you use on a dozen sites. The same one you used to order flowers three years ago on a local boutique’s site. The same site whose password database was quietly hacked last week.
The Internet is a wild place

Most people on the Internet only see the tip of the iceberg. They’re on Netflix, Google, YouTube. They’re playing mobile games, ordering from Amazon. The Internet is like a giant mall with the best shops and arcades.
There’s more to the Internet than you may see. Darknets, where identities, weapons, drugs, and the darkest of pornography can be bought and sold. Cyberwarfare and espionage between countries of all sizes. Enormous “botnets,” or networks of compromised computers just like yours that are used to attack networks and crack passwords. Teams of hackers who work to find vulnerabilities in sites or in people and exploit them for amusement, financial gain, or just to make a statement.
This isn’t a reason to fear the Internet, to fear shopping online or visiting new places. This is a reason to respect it, and to be safe.
The line of fire
“But nobody will come after me!” you might think. “I’m not important. Who would target me?”
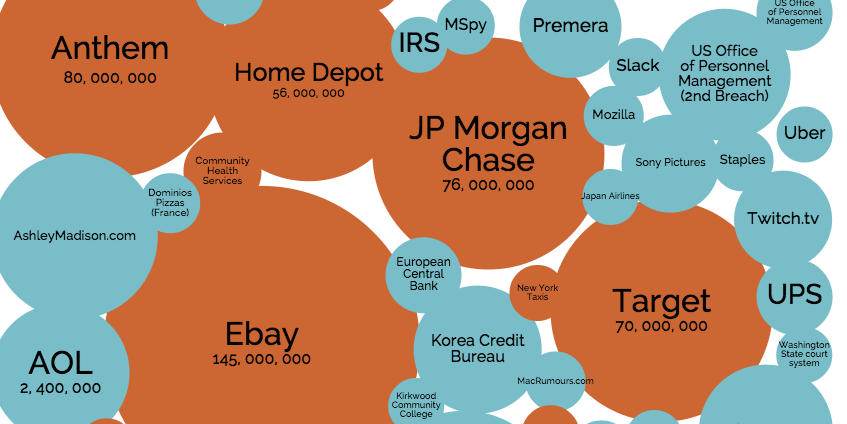
The problem with that line of thought is that it assumes a person is going after you specifically. That’s often not the case. Hackers and botnets go after many, many websites. They’re looking to hit the motherload. For instance, here’s some of the bigger sites hacked lately, and how many people were affected:
- Steam – 35 million
- Evernote – 50 million
- Home Depot – 56 million
- Target – 70 million
- JP Morgan Chase – 76 million
- PlayStation Network – 77 million
- Anthem – 80 million
- eBay – 145 million
Ever use any of these? Me too.
So what happens next? Well, automated systems will harvest the results and begin trying these combinations of usernames/passwords on all sorts of different sites. Google/gmail, banks, dating sites, anywhere. And how big are these botnets? They can reach up to the 10s of millions of computers.
You are not specifically being targeted, but you’re in the line of fire. And this is going to keep happening, over and over again.
So let’s protect you from this. I’m going to teach you about three things:
- Using passwords safely
- Two-factor authentication, a second layer of protection and alert system
- Identifying and ensuring secure connections to websites
And in case you’re wondering, yes, you are the target of my post. So keep reading.
Passwords: Your first line of defense

Most people on the Internet treat passwords like they’re a cute little passphrase to get into a clubhouse. We’re trained by our computers to pick something memorable to log us into our desktops, a code that “protects” you from others in the house who might want to check your e-mail. Much like a standard lock on your door protects you from your neighbors simply walking in.
Nobody ever really teaches us properly. It’s common to use your dog’s name as a password, or your birthdate, or something equally easy to remember and crack. It’s also common to use the same password or set of passwords on many different sites and services, which is how our fictitious Friday night was ruined.
This is extremely important to get right. Here are the rules for protecting yourself using passwords:
- Never use the same password for more than one site.
- Pick a long, strong password with uppercase and lowercase letters, numbers, and symbols, without any dictionary words.
That’s basically it. Seems simple enough in theory, but how do you keep track of all those passwords? You’d probably have 50 of them!
Don’t worry, there are tools that make this super easy.
1Password
This is one of my favorite tools for staying secure.
1Password is a tool for keeping track of your accounts and generating new passwords. It works with your browser and remembers any password you enter, and makes it really easy to fill in passwords you’ve already entered.
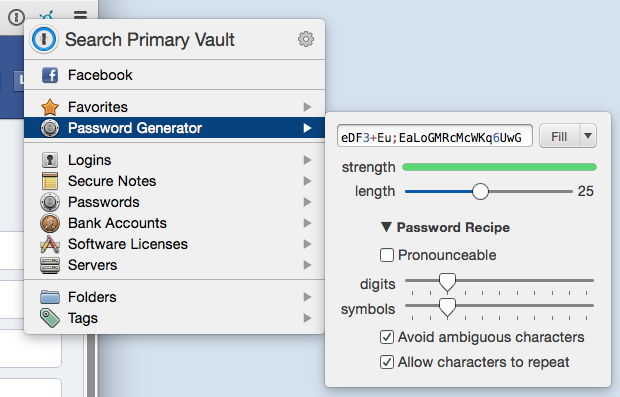
When you’re creating a new account or changing passwords, it’ll help you by generating strong, secure, nearly uncrackable passwords. For example, here’s one it just made for me: wXXgVzb8Zp(zwmjG7zBGkg=iT.
It’s available for Mac, Windows, iPhone, iPad, and Android. It’s free for iPhone, iPad, and Android, and costs only $35 for Mac and Windows (which is a bargain for what you’re getting).
Let me show you how it works.
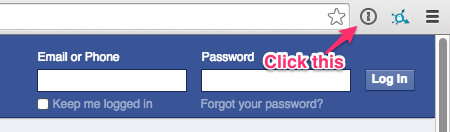
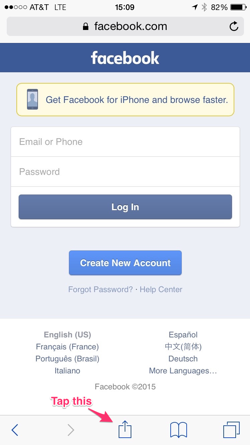
I’m about to log into an account on Facebook.
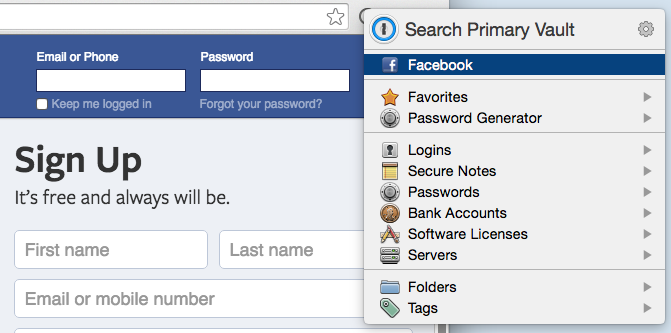
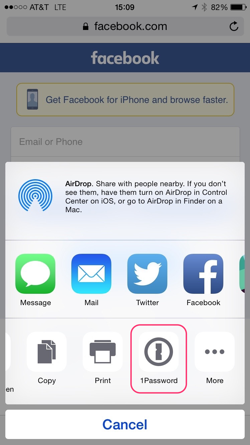
Instead of typing my login and password, I just click that little keyhole icon next to the address bar, which will pop up any 1Password entries I have for Facebook.
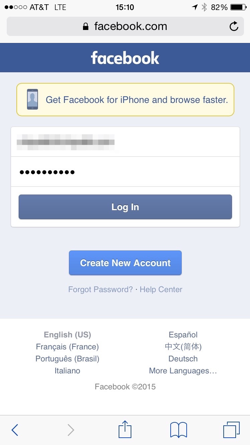
Once I click “Facebook,” it’ll fill in my username and password and log me in. It’s just that simple.
When you’re signing up for a new account, use the Password Generator, like so:
Once you create the account, 1Password will remember the password for later. Look at that thing. Nobody’s cracking that!
This all works for any site, and even works on your iPad/iPhone:
1Password is great for more than passwords. It can keep secure notes, information on your credit cards or bank accounts, or really anything else you have that you want available but locked away.
In order to access your stuff in 1Password, you only need to remember a single password of your choosing. Make sure this is a strong one, and that you don’t forget it! Write it down if you have to.
Buy 1Password and use it. Look, $35 is nothing compared to the potential fallout of being involved in the next several major security breaches.
LastPass
LastPass is an alternative to 1Password, and is great if you’re an Android user. Usage is pretty similar to 1Password.
I don’t personally have a lot of experience with LastPass, but a lot of people love it. You can learn more about it on their site.
Pen-and-paper password journal
I’m sure you’ve been told before that it’s a bad idea to write down your passwords, am I right? Afterall, if you write them down, then gee, anyone can get them!
That’s not entirely true. The fact is, you’re more at risk reusing one or two weak passwords on the Internet than keeping dozens of strong passwords written down on paper in your home.
Let’s be clear, this is not the best option, and if you’re going to do this, keep it secret, keep it safe. Still, it’s better than not having strong passwords. If at all possible, use 1Password or LastPass, but if you absolutely must, write them own on a dedicated journal that you can keep safe somewhere. Don’t lose it, and always use it for every password.
Two-Factor Authentication: Second line of defense

You’re now using stronger passwords, and you have friendly tools to help manage them. Good job! The next step is making sure that only you can log into your most important websites.
Many sites and services (Google, Apple, Dropbox, Evernote, Bank of America, Chase, and many others) offer an extra security layer called “two-factor authentication.” This is a fancy term for “We’ll only log you in if you enter a code we’ll send to your phone.” When enabled, these services will require something you know (your login/password), and something you have (your phone).
Let’s take Google, for example. You can set things up so that after entering your username and your brand-new secure password, Google will send you a text message with a 6-digit code. Once you receive the text (which only takes a second), you’ll enter it on the site, and you’ll be logged in.
Now why would you do that? To prove that you are the one logging in, and not someone who’s figured out your password. The cell network’s going to make sure that text is only going to your phone, and you’re going to prove it’s you logging in. (Some services will require that you use a specialized app, or a hardware device that fits on your keychain, but most will work with text messages.)
Imagine someone did get a hold of your password, and tried logging in. You’re still going to get that text, but that person will not. He/she won’t be able to log in as you. You’re safe! It’s also going to be a dead giveaway that your password was compromised. You’ll want to change it right away.
Basically, this is both your gated community and your alarm system.
This is pretty easy to set up at most places. Here are some guides:
- Apple
- Bank of America
- Blizzard
- Dropbox
- Evernote
- E*Trade
- Microsoft Office 365
- Outlook.com
- PayPal
- Snapchat
- Steam
You can find more at twofactorauth.org. Just click the icon under “Docs” for any service you use that’s green.
I’ll be honest with you, this will feel unfamiliar at first, and you might be tempted not to do it. Trust me, though, this is worth turning on for as many services as possible. You’ll be glad you did next time one of these companies announces a security breach.
Identifying and ensuring secure websites
Let me briefly explain how the Internet works.
When you connect to a website, the browser will usually try to access it first over the “HTTP protocol.” This is the language that browsers and web servers speak. This communication is in plain text, which means anybody that listens in can read what’s being posted. This is sort of like handing a piece of paper to someone, and having them pass it along to the next person, and so on, until it reaches its final destination.
That’s very bad if you’re sending anything confidential. Passwords, for instance. It’s important that you learn to identify when you’re on a secure website.
You know the address/search bar on your browser? Look to the left. If you see http://, or you don’t see anything but an icon and a domain name, you’re on an insecure website.
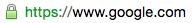
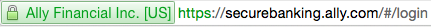
However, if you see https://, or a lock icon, or a green banner, you’re good! This is using HTTPS, an encrypted connection, meaning that nobody in-between can listen in. That’s more like writing your letter in gibberish that only you and the final recipient understand.
For comparison, these are secure:
This is not:
Always look for these before filling out any forms. If it’s not showing a green banner or lock, you don’t want to give the site any sensitive information.
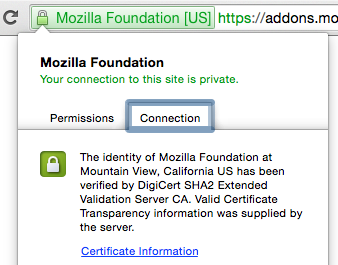
If you see a green banner, it’ll show the name of the company or organization. This is showing that the encrypted channel and website have been verified by a “certificate authority,” an entity that issues certificates for these encrypted channels. It means they’ve checked that, for instance, ally.com is owned by Ally, and not by someone pretending to be Ally.
If you click the banner or the lock icon, you’re going to see some more information about the connection. Most of this will be highly technical, but you should see some blurbs about who verified the authenticity of the site, and some information on the organization owning the site.
Most websites these days are moving to encrypted HTTPS connections, and most will automatically redirect all requests from HTTP to HTTPS. This is good, but you can go a step further and have your browser always start out using the HTTPS connection whenever possible. This takes almost no effort, and is worth doing.
This is done with a browser extension called HTTPS Everywhere.
If you’re running Chrome as your browser, simply install it from the Chrome store.
If you’re running Firefox, install it from the Firefox add-on store.
Did you do it? Great, you’re done! You’re now a little bit safer on the Internet!
Putting it all together
I threw a lot of information at you, but hopefully you’ve learned a lot and will put it into practice.
So let’s summarize. If you follow the above, you’ll:
- Be at less risk for identity and financial theft the next time there’s a major security breach, since your passwords won’t be shared.
- Be alerted when someone tries to log in as you on any service with two-factor authentication enabled.
- Have passwords strong enough to be unguessable and nearly uncrackable, for all sites and services you use.
- Know how to identify secure websites, so you don’t leak passwords or other private information to anyone who’s listening in.
- Automatically connect to the most secure version of a website whenever possible.
Not bad for a little bit of work. Hopefully by now, you realize that this does matter, because you, I, and everyone else really is a target, simply because we’re all part of something large enough to be a target.
So pass this around. Tell your friends about what you’ve learned. Educate your kids. Stay safe on the Internet.


Hi there,
I’m Eva and I work for AgileBits, the makers of 1Password.
I wanted to thank you for taking the time to educate your readers on the importance of password managers and online security, and for including 1Password in your discussion!
In this day and age, it is so important that we all use strong and unique passwords for every site that we visit, and password managers can help make it much more convenient to be secure.
Keep sharing the secure word!
Eva Schweber
Good Witch of the Pacific Northwest @ AgileBits
support.1password.com
Hey thanks for replying, and for such a great product! 🙂 I had to hold myself back from going into a bunch of other 1Password features, like multiple vaults (<3).